Since 2006, AT&T has operated and managed Bellsouth, a popular dispatch service. Bellsouth, a well-known American poet, has been furnishing services to further than 18 nations for further than a decade. Since Bellsouth intermingled with AT&T, you’ve been suitable to pierce your Bellsouth dispatch account through the AT&T login runner.
Bellsouth has been an attachment of AT&T, and it’s known for its high-speed internet services. Likewise, Bellsouth (an attachment of one of the world’s leading telecommunications enterprises) is a well-known dispatch service provider. This dispatch program has a large stoner base because it has handed services in multitudinous nations.
This companion will educate you on how to log in to your Bellsouth dispatch account using a simple way so that you do not have any problems.
How to Access Your Bellsouth Dispatch Account:

Given that Bellsouth is possessed and managed by AT&T, you will need to go to the AT&T login runner to finish the procedure. As a result, if you go to the AT&T sign-in website looking for the BellSouth dispatch login runner, you’ll be taken to the AT&T sign-in runner.
The following are the entire Bellsouth.net login instructions
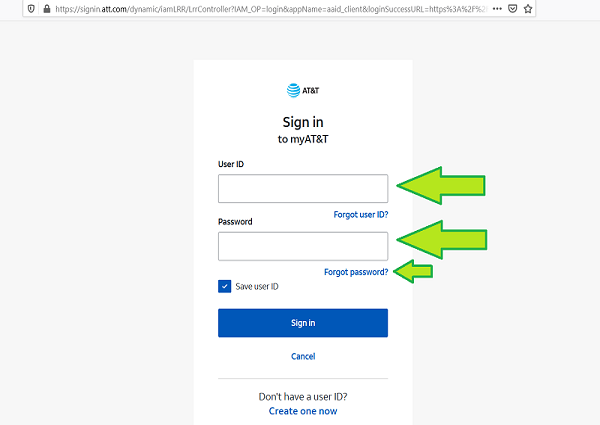
Go to the AT&T Mail Login runner to get started.
Enter your Bellsouth username and word in the Stoner ID and Word textbook areas.
Also, to log in to your Bellsouth dispatch account, click’ Subscribe in.’
Likewise, Yahoo and AT&T have joined to give better dispatch services, and because AT&T owns Bellsouth, you can subscribe in using any of the following links. So, if you were seeking for thewww.bellsouth.net login runner to pierce your Bellsouth dispatch account, keep in mind that it no longer exists.
Using a dispatch customer, log in to BellSouth.
Still, you will need the following dispatch garcon settings, If you wish to use a dispatch customer to set up and log in to your Bellsouth dispatch account.
POP3
POP3 account type
- Number of anchorages995
- Outbound.att.net is the gregarious correspondence garcon.
- Number of anchorages 465
- SSL (Secure Socket Layer) encryption
IMAP
Type of account IMAP
- Imap.mail.att.net is the incoming correspondence garcon.
- 993 is the harborage number.
- SMTP.mail.att.net is the gregarious correspondence garcon.
- Number of anchorages 587
- SSL (Secure Socket Layer) encryption
You may fluently pierce your Bellsouth net dispatch account using these settings.
Issues with Bellsouth Dispatch Login:
You may be unfit to pierce your Bellsouth dispatch account for a variety of reasons, including forgetting your username or word or being inactive for further than 6 months, which may affect your account being firmed.
Then are some of the reasons why you could be having trouble logging in to your Bellsouth correspondence customer
1. Error in authentication
When you’re unfit to confirm your identity to the dispatch program, an authentication issue(error) occurs, and you’re unfit to pierce your account as a result.
2. Dispatch from Bellsouth is not responding:
Still, you will notice that BellSouth dispatch is not responding at each, and you will not be suitable to pierce your account if the waiters are down.
3. The login runner doesn’t appear to be lading:
When you try to login into your Bellsouth dispatch account, a slow internet connection can beget problems.
4. The username or word has been entered inaptly:
You will have trouble logging into your account if you do not remember your username or word.
5. There has been a breach of security on the account:
Still, it’s likely that someone differently has changed your account word, and you’ll be unfit to pierce your emails for the time being if you’re unfit to log in indeed after entering the right Bellsouth account word.
6. Account has been locked due to multiple failed login attempts:
Entering the wrong word multitudinous times is in no way a good idea because your Bellsouth account will be locked and you will not be suitable to check in for several hours. Simple troubleshooting, similar as changing the word, switching to a new cyber surfer, or just clearing the cyber surfer’s history and eyefuls, can fluently resolve Bellsouth.net Login issues.
Word Reset for BellSouth Dispatch Account
Utmost Bellsouth consumers are concerned about how they will regain their account word if they forget it or if someone fresh changes it.
The answer is straightforward whenever your account becomes inaccessible, you must reset your word. It’s generally a good idea to change your Bellsouth word on a regular basis to avoid playing attempts.
How they’ll be suitable to recover the same:
The answer is straightforward whenever your account becomes inaccessible, you must reset your word. To avoid playing attempts, it’s voguish to contemporize your Bellsouth word on a regular base; but, if you’re in a need, you can reset your word using the information handed.
1. Click ‘Continue‘after entering your Stoner ID, which is your Bellsouth login, and your last name.
2. The’ Find your Word’ runner can be factory by going to the AT&T Word Reset Link.
3. You must now conclude a system for entering a ‘Temporary Word,’ analogous as text or dispatch.
4. Enter the temporary word and click ‘Continue‘once you’ve entered it.
5. You’ll be suitable to change the word for your Bellsouth dispatch account now.
BellSouth was founded as the holding company for the telephone operating companies in the southern region of the old Bell System — Atlanta- rested Southern Bell and Birmingham, Alabama- rested South Central Bell — as part of the separation of the old AT&T in 1984. In effect, the conformation of BellSouth reconnected the maturity of telephone service in the Southeast United States. Until 1967, when the western portion of its service zone came to South Central Bell, Southern Bell was the Bell System operating company for the entire Southeast.
Southern Bell and South Central Bell introduce BellSouth Services, a shared services establishment, to give centralized operations like engineering and information technology. Telephone and DSL/ Dial-Up Internet services are available in the BellSouth operating area in Alabama, Florida, Georgia, Kentucky, Louisiana, Mississippi, North Carolina, South Carolina, and Tennessee.
Agreement :
AT&TI NC. Announced its significant deal to buy BellSouth Corp. on March 5, 2006. Following the termination of the merger, BellSouth became a fully owned subsidiary of AT&T Inc. On December 29, 2006, the accession was finalized. On June 30, 2007, BellSouth Telecommunications ceased conducting business under the BellSouth brand. AT&T Alabama is the new name under which it operates. Florida AT&T. After the United States Department of Justice ordered the American Telephone & Telegraph Company to divest itself of its indigenous telephone firms on January 1, 1984, BellSouth was one of the seven original Regional Bell Operating Companies. AT&TI Inc. blazoned a junction on March 5, 2006, and implemented it on December 29, 2006.
Contended NSA cooperation:
In 2006, USA Today released an article that incorrectly stated that three of the top US carriers, including BellSouth, had been providing the National Security Agency with call logs for all international and domestic calls. According to the composition, this data is being utilized to create “the biggest database ever assembled.” On May 16, 2006, BellSouth issued a statement saying that no contract with the NSA existed and that they had never given the NSA anything comparable to call logs. On June 30, 2006, USA Today reported that “On May 15, BellSouth claimed it couldn’t absolutely deny involvement in the scheme until it had performed a comprehensive disquisition.” According to BellSouth, an internal inquiry determined that the business did not contract with the NSA or send over call logs.
BellSouth stops displaying frequenter ID from Sprint guests:
BellSouth guests no longer accept frequenter ID information from Sprint PCS guests as of January 1, 2006. In general, every incoming call from a Sprint PCS mobile phone will display the City, State format on the frequenter ID display rather than the person or company name linked with that number. Based on a 1996 agreement between Sprint and BellSouth, this is most likely the consequence of a ten-year deal. Sprint sued BellSouth for $ 20 million in 2003, saying BellSouth breached a 1996 contract by failing to provide Sprint frequenter-identification information to BellSouth visitors. Analogous frequenter ID “deals” have been left to the consumer to battle for what they should have shown on their frequenter ID device, either with their own carrier or through government nonsupervisory bodies. Sprint and SBC Dispatches couldn’t agree on freights charged to carriers to look up in 2002. Mission To improve dispatches among BellSouth seniors and to provide a venue for BellSouth retirees’ voices to unite as one. The BellSouth Retirees Association intends to bring the issue of protecting promised benefits to the attention of BellSouth’s executives and demand that they listen.
Merge:
The AT&T/BellSouth merger is simply the latest indication of the irrelevance of antitrust in a rapidly changing global competitive environment. In telecommunications, the changes in the competition have come from an explosion in technology and at least partial freedom from the suffocating embrace of government regulation. After the merger is approved and closed, each outstanding share of BellSouth common stock will be exchanged for 1.325 shares of AT&T stock. All BellSouth shareholders will, therefore, become shareholders of AT&T. No action will be required by you until after the closing of the merger. A government big enough to bestow a monopoly is big enough to take it away. In 1974, the U.S. Justice Department filed an antitrust lawsuit against AT&T based on complaints by MCI and other long-distance service providers. … The lawsuit went unresolved for eight years.
BellSouth was the final of the Regional Bell Operating Companies to maintain its original commercial name following AT&T’s separation in 1984, as well as the last to have the Bell hallmark as part of its major commercial brand.
From 1993 to 1998, BellSouth operated in New Zealand as BellSouth New Zealand Limited before being bought by Vodafone and renamed Vodafone New Zealand. It was in competition with Telecom New Zealand. BellSouth Australia Pty Limited was the company’s name in Australia. Telephonic bought all of Bellsouth’s Latin American means in late 2004 for about $5.85 a billion.
BellSouth established BellSouth Services as a participated services establishment to give centralized operations similar to engineering and information technology to Southern Bell and South Central Bell. Telephone and DSL/ Dial-Up Internet services are available in the countries of Alabama, Florida, Georgia, Kentucky, Louisiana, Mississippi, North Carolina, South Carolina, and Tennessee. Satellite TV service was made available through cooperation with DirecTV. BellSouth Entertainment supplied string TV ( generally via MMDS) in many metropolises (as part of the Americast adventure).
BellSouth composite South Central Bell and BellSouth Services in 1992 to come to Southern Bell, which was renamed BellSouth Telecommunications. This redounded in the conformation of a single operating company in the BellSouth zone, effectively reuniting Southern Bell and South Central Bell. Still, until 1998, BellSouth used the Southern Bell name within the eastern section of its area and therefore the South Central Bell moniker within the western portion until it named BellSouth as its single client-facing brand.
The company’s primary operations capitals remained in Atlanta and Birmingham. Atlanta and Birmingham were also the primary locales for indigenous headquarters operations. Birmingham, Miami, Atlanta, Louisville, New Or leans, Jackson, Charlotte, Columbia, and Nashville all had state-wide operations centers. BellSouth Mobility has headquarters in Atlanta, Georgia, and Birmingham, Alabama.
BellSouth reorganized itself in two critical areas at the end, wireless and broadband. In 2001, they intermingled its wireless operation, BellSouth Mobility, with SBC’s wireless services, and bought a 40 interest in the arising establishment, Cingular Wireless. The new establishment reckoned for a sizeable portion of BellSouth’s profit. This collaboration continued when SBC acquired the old AT&T and renamed it AT&T Inc. A significant end for the pot was to continue adding broadband penetration and operations in the consumer sector. These endeavors were incompletely supported by the trade of Latin American operations.
You May Also Like:
Ultimate Guide On Quick Login to An AOL E-Mail Account